What is the NIST CSF?
The National Institute of Standards and Technology (NIST) is a non-regulatory agency of the United States Department of Commerce. The NIST provides technical support to industry, government, academia, and other organizations in a wide range of areas, including cybersecurity, information technology, physical sciences, engineering, and manufacturing. NIST is also responsible for developing and maintaining measurement standards and promoting the use of these standards to ensure accuracy and consistency in scientific and engineering measurements.
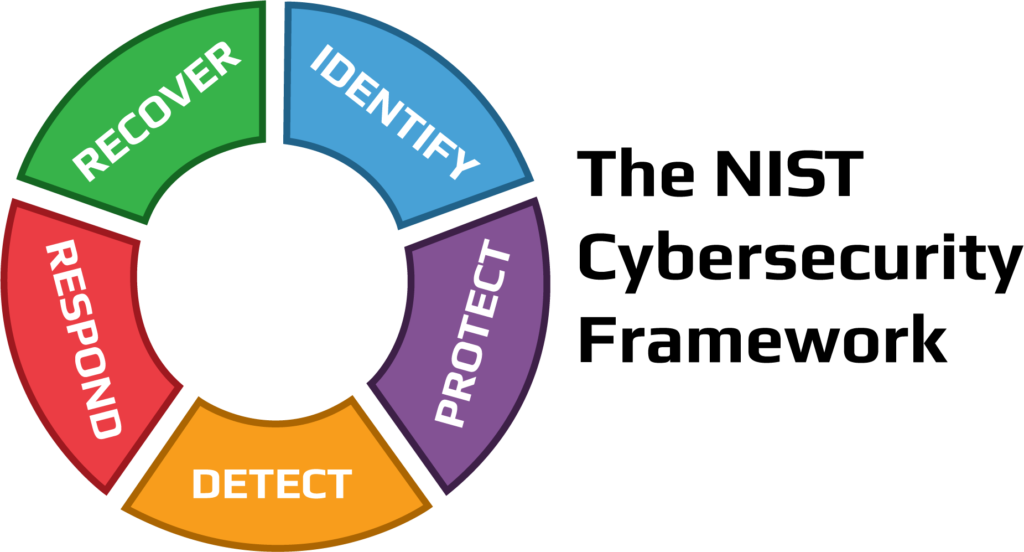
The NIST Cybersecurity Framework (CSF) provides a set of guidelines, best practices, and standards that can help organizations of all sizes and industries manage and reduce cybersecurity risks. The framework consists of five core functions that are designed to help organizations understand their current cybersecurity posture, develop a cybersecurity strategy, and implement a plan to manage risks.
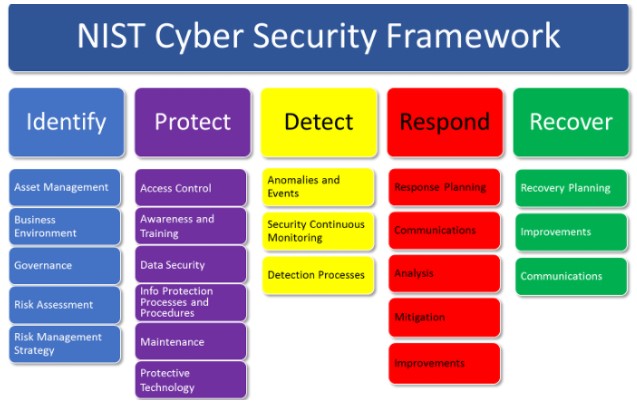
- Identify: This function involves understanding an organization’s cybersecurity goals and objectives, identifying critical assets and systems, and developing a risk management plan. The risk management plan should identify the potential threats and vulnerabilities that could impact an organization’s critical assets and systems, and provide a roadmap for addressing those risks. This function is critical because it provides a foundation for the other core functions of the framework.
- Protect: This function involves implementing measures to safeguard critical assets and systems from potential cyber threats. Measures may include access control, data encryption, and security policies and procedures. This function is important because it helps prevent potential cyber attacks from being successful. It is much easier and less costly to prevent an attack from occurring than to recover from one.
- Detect: This function involves monitoring an organization’s systems and networks to identify potential cybersecurity incidents. Detection measures may include firewalls, intrusion detection systems, and antivirus software. This function is important because it enables an organization to quickly detect and respond to potential threats. Early detection can help limit the damage caused by a cyber attack.
- Respond: This function involves developing an incident response plan and taking action to contain and mitigate the impact of cybersecurity incidents when they occur. The incident response plan should outline the steps that an organization will take in the event of a cybersecurity incident. This function is important because it enables an organization to quickly respond to a cyber attack and limit the damage caused.
- Recover: This function involves developing and implementing plans to restore systems and networks to normal operations after a cybersecurity incident. The recovery plan should outline the steps that an organization will take to restore critical assets and systems to normal operations. This function is important because it enables an organization to quickly recover from a cyber attack and minimize the impact on business operations.
The framework is designed to be flexible and scalable, enabling organizations of all sizes and industries to create a comprehensive cybersecurity plan that addresses their unique risks and vulnerabilities. The framework is also aligned with other cybersecurity standards and guidelines, such as ISO 27001 and NIST SP 800-53. This alignment makes it easier for organizations to adopt the framework and integrate it into their existing cybersecurity programs.
By following the framework’s core functions, organizations can establish a strong cybersecurity posture that helps protect critical assets and systems from potential cyber threats. The framework also encourages organizations to continuously assess and improve their cybersecurity programs, ensuring that they remain effective in the face of an ever-evolving threat landscape.
Alignment with the NIST Cybersecurity Framework
Alignment with the NIST Cybersecurity Framework refers to how well an organization’s cybersecurity program matches the framework’s core functions and best practices. The framework provides a set of guidelines and standards that organizations can use to develop and implement a comprehensive cybersecurity program. By aligning their cybersecurity program with the framework, organizations can ensure that they are addressing the most critical aspects of cybersecurity and effectively managing their cybersecurity risks.
Alignment with the framework involves several key steps:
- Identify the organization’s cybersecurity goals and objectives: The first step is to understand the organization’s overall goals and objectives for cybersecurity. This may involve identifying critical assets and systems, determining potential threats and vulnerabilities, and developing a risk management plan.
- Review the framework’s core functions and best practices: The next step is to review the NIST Cybersecurity Framework’s core functions and best practices. This includes understanding the five core functions of Identify, Protect, Detect, Respond, and Recover, as well as the various categories and subcategories of best practices.
- Assess the organization’s current cybersecurity posture: Once the core functions and best practices have been reviewed, the organization should assess its current cybersecurity posture to determine how well it aligns with the framework. This may involve conducting a gap analysis to identify areas where the organization falls short of the framework’s recommendations.
- Develop a roadmap for alignment: Based on the gap analysis, the organization should develop a roadmap for aligning its cybersecurity program with the framework. This may involve identifying specific actions that need to be taken to address gaps and improve cybersecurity posture.
- Continuously monitor and improve cybersecurity posture: Finally, the organization should continuously monitor and improve its cybersecurity posture to ensure that it remains aligned with the framework. This may involve regularly reviewing and updating policies and procedures, conducting cybersecurity training for employees, and implementing new cybersecurity controls as needed.
Alignment with the NIST Cybersecurity Framework is important because it provides a standardized approach to managing cybersecurity risks. It also enables organizations to benchmark their cybersecurity program against industry best practices and improve their cybersecurity posture over time. Additionally, alignment with the framework can help organizations demonstrate their commitment to cybersecurity to customers, partners, and other stakeholders.
How to use the NIST Cybersecurity Framework
The NIST Cybersecurity Framework provides a set of guidelines and best practices for managing cybersecurity risks. Here are the steps organizations can take to effectively use the framework:

- Understand the Core Functions: The first step in using the NIST Cybersecurity Framework is to understand its core functions. These five core functions are Identify, Protect, Detect, Respond, and Recover. They are designed to help organizations manage their cybersecurity risks by identifying critical assets and systems, protecting those assets, detecting and responding to cybersecurity incidents, and recovering from those incidents.
- Conduct a Risk Assessment: The next step is to conduct a risk assessment to identify potential threats and vulnerabilities to the organization’s critical assets and systems. This may involve reviewing previous cybersecurity incidents, analyzing the organization’s IT infrastructure, and identifying potential risks and vulnerabilities.
- Develop a Cybersecurity Plan: Based on the risk assessment, organizations should develop a cybersecurity plan that aligns with the NIST Cybersecurity Framework’s core functions. The plan should include specific actions and best practices that the organization will implement to manage cybersecurity risks.
- Implement Cybersecurity Controls: Once the cybersecurity plan has been developed, the organization should implement cybersecurity controls to protect its critical assets and systems. This may include implementing firewalls, intrusion detection and prevention systems, and security monitoring tools.
- Monitor and Assess Cybersecurity Controls: Organizations should regularly monitor and assess their cybersecurity controls to ensure that they are effective in mitigating cybersecurity risks. This may involve conducting regular penetration testing, vulnerability scans, and security assessments.
- Respond to Cybersecurity Incidents: In the event of a cybersecurity incident, organizations should follow the NIST Cybersecurity Framework’s response procedures to quickly contain and mitigate the incident. This may involve isolating affected systems, identifying the cause of the incident, and implementing remediation measures.
- Continuously Improve Cybersecurity: Finally, organizations should continuously improve their cybersecurity posture by reviewing and updating their cybersecurity plan and controls as new threats emerge. This may involve conducting regular cybersecurity training for employees, adopting new best practices, and staying up-to-date on the latest cybersecurity trends.
By following these steps, organizations can effectively use the NIST Cybersecurity Framework to manage their cybersecurity risks and protect their critical assets and systems.
